Data Security
There are also some things you can do yourself to protect your own data,but lets look at some of the places where data may become insecure or where your PC may have “Achilles Heels” and someone may gain access to it.
There are two main areas that you may like to think about.
Of these,possibly it is the online case that concerns people the most,since
this is usually where they are entering personal details and security numbers
and passwords.However,it maybe worth thinking about how to protect your computer
even when it is not connected to the internet.
When connecting to the internet you may like to consider the following stories which raise issues about data security (taken from www.geocities.com/templarser/metro30.html)
I was a teenage hacker |

The arrest of Briton Gary McKinnon, accused of hacking into computer systems
at the Pentagon and Nasa, has again thrown the spotlight on the world of
hi-tech crime. The problems he allegedly perpetrated cost more than
£500,000 to track and correct. @metro editor JONATHAN GODDARD tries
to find out why hackers do it.
FORMER hacker LC uses his skills to help police,
private companies,and the FBI tackle the problem of hacking. Now 21, the
security consultant was in trouble for credit card fraud and hacking into
his school's computer systems between the ages of 13 and 15. 'Anyone can
connect up to a server, discuss whatever they want and no one can regulate
it,' says LC.
'I started getting into piracy and was then
introduced to hacking' groups. 'I wasn't in trouble work-wise at school,
but was a
geek.
The only way I could really excel was to be this hacker. Police were more
interested in how a 15-year-old did these things than messing up my future.'
Hacking has been a serious problem to computer
systems and sensitive information for many years.
'And there are bad types - the script kiddies
and malicious hackers, who make money from it.'
Most malicious hackers break into shopping
sites and steal credit card numbers. 'Gary McKinnon most likely didn't know
what he was doing,' adds LC. A hacker breaks into a system, gains knowledge
and keeps control of that system or disappears.
'Nowadays you have tools you can download
that, within 20 seconds, allow anyone to start scanning at the press of a
button. It's a power buzz'
IT security consultancy Information Risk
Management recently probed the online defences of 18 online banks including
Barclays, HSBC, and Lloyds TSB, and found 72 per cent of them were vulnerable.
The need for banks to protect against cyber-crime
was highlighted in March when police foiled an attempt to steal £220million
from a London-based Japanese bank, Sumitomo Mitsui.
Hackers are breaking into about 30,000 PCs
a day to send viruses around the globe or reveal bank account details -
phishing.
LC says the problem is a slow reaction to
security threats.
'We need a system worldwide which every government
agrees on,' he adds.
'It's like earthquakes - you're never going
to stop them, but you can minimise the damage.'
[Metro, June 13,2005]
Conmen 'phish' in your e-mail
inbox
BY SARAH GETTY
ALMOST half of all Internet users have received
spam emails aimed at tricking them out of money, a new poll by AOL found.
'Phishing' e-mails - designed to look like
they come from a bank -ask users for their personal information and password
details. Fraudsters can use the information to steal cash from users' accounts.
The techniques being used are becoming increasingly sophisticated, with e-mails
often directing users to false websites via hyperlinks. Yet there is little
chance of getting money back if you are caught out by a phishing e-mail.
More than half those who lost cash were not
compensated by their bank or credit card provider. The amounts stolen
are often small - about £50 - because the conmen aim to carry on undetected.
They know that few people check credit card and bank statements thoroughly.
Other online scams include paying for items
ordered over the Internet which never arrive and sending cash following a
demand from a bogus e-mail.
Will Smith, from
AOL,
said: 'It is often difficult to spot a scam so it's crucial people protect
themselves.' AOL's advice includes:
·
Use spam filters,
anti-virus software and firewall software
·
Be suspicious, especially
of unsolicited e-mails
·
Do not click on links
if you are suspicious - type in the company's web address instead
·
Check your bank balance
and statements regularly.
[Metro May 3, 2005] |
Teenager cracks e-mail code |
 |
Sarah Flannery, 16, who baffled the judges
with her grasp of cryptography They described her work as
"brilliant" |
BY AUDREY MAGEE, IRELAND CORRESPONDENT
|
An Irish schoolgirl
was yesterday hailed as a mathematical genius after devising a code for sending
secret messages by computer. |
Hackers unravel key to
Internet
Hackers have attacked US army and NASA computers
after stealing codes which control the Internet. The gang is thought to have
exposed security flaws in the networks but it is not known how much
data was stolen or destroyed. The attackers are believed to have been based
in Europe and have targeted thousands of computers some serving research
labs. The revelation follows the latest arrest over last May's theft of program
instructions for machines which control the Internet. The suspect,detained
in Sweden on Monday,is believed to be a 16-year old already charged with
hacking into a university. The stolen CISCO SYSTEMS code was posted on the
Net.
[Metro May 11,2005]
BY SARAH HILLS
HACKERS have unleashed an 'industrial-strength'
attack in a bid to steal sensitive information from almost 300 Government
departments, it emerged yesterday.
Businesses have also been targeted during
months of concerted attacks, which are launched from bogus e-mails and contain
a 'Trojan' attachment.
At first glance they appear harmless but,
once opened, an invader can gain fill' control of the user's machine.
A 'recent rise in sophistication' in attacks
on financial, telecommunications, energy, transport and health organisations
has been noted by the National Infrastructure Security Co-ordination Centre.
The Government body aims to protect essential
services and systems from electronic attack.
It issued a warning yesterday urging businesses
to beef up security. 'There are businesses on the periphery of the critical
national infrastructure that can be targeted by these attacks,' it confirmed.
These could include banks,insurers and other financial units. 'This is not
a few hackers sitting in their bedrooms trying to steal bank account details
from individuals. This is aimed at organisations, targeted at gaining information
and is extremely well organised and structured,' said NISCC director Roger
Cumming.
Security consultant Carole Theriault, who
helped the NISCC analyse the Trojans, said there were 17 types.
'They were basically information-stealing
files hidden in the machines. It must have been serious enough for the NISCC
to put a warning out,' she added.
Many of the messages were sent from addresses
in Asia and efforts are now being made to shut them down.
The messages are spoofed to appear as though they come from a credible source and hackers use distribution lists to target large numbers of people. Nothing significant has been stolen so far, said the NISCC.
BY OLIVER STALLWOOD
The con is believed to originate from Nigeria.
PayPal and eBay yesterday said its safeguards were 'a world class example
of the tools that can be put in place to prevent these attacks'.
Members suspecting a hoax email should send
it to
spoof@ebay.co.uk
or
spoof@paypal.co.uk.
Within a few minutes, they will get a response
confirming whether or not it is genuine. |
SUPERBUG THREAT TO COMPUTER NETWORKS BY JO STEELE |
| MAJOR companies are at risk from a crippling new computer bug which targets
their anti-virus software, it was revealed last night. Already, a division
of the world's biggest media corporation, Time Warner, has heen hit. Experts
believe a disgruntled hacker with a grudge against software firm Symantec
is behind the new trojan virus, a version of the 'Rinbot' bug. The US company designs anti-virus packages for major corporations. The 'worm' works by exploiting security loopholes in anti-virus software. It then spreads through the network by manipulating 'weak' spots such as simple passwords. Once the virus is embedded, it takes over many other computers forming a 'zombie' network. Graham Cluley, a senior technology consultant with IT security firm Sophos, said: 'Traditionally hackers always went after Microsoft's anti-virus programs. But now they're targeting other programs such as Symantec's.' He added: 'Without you knowing it, hackers will use your computer for a variety of purposes like sending out spam, or distributing denial of service attacks, or even blackmailing other websites.' Mr Cluley said the strain appeared to be hitting networks that run Microsoft Windows operating system. He added: 'We do know that it has hit CNN Time Warner in the US. That's the most high-profile place but we are aware of it hitting elsewhere.' Syrnantec said its Norton products were not affected and it had released new protection against the virus yesterday morning. [Metro Mar 2,2007] |
ONLINE SECURITY
From the above stories it may be gleaned that some of the issues concerning
online data security might be
- Phishing - The attempt to get bank details using fraudulent Email requests.
- Hacking – Breaking into computer systems by breaching security measures.
- Firewalls – Limiting access to minimise security breaches.
- Trojans/worms/viruses – Programs that attempt to damage computer files.
- SPAM - Unsolicitied mail sent to your inbox.
- Encryption – Techniques to render data secure. Anti-virus software can be installed.
- Secure sites – Some sites need to be more secure than others.Some denote this with a small “padlock” symbol in the corner of a webpage.
- Passwords – Using codewords to defeat unauthorised entry.
Note that there are also ways that your movements on the web can be tracked by data being stored automatically on your computer. “Cookies” are small data files which store data on your access to websites.”Adware” can also exist on your system which can enable pop-ups to crop up when accessing websites.
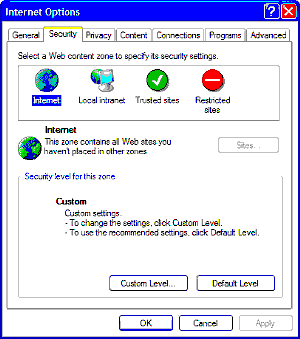 Internet Explorer and Security
Internet Explorer and Security
With specific respect to Internet
Explorer,the security controls can be found under the TOOLS menu
and INTERNET OPTIONS.The Tabs CONTENT,PRIVACY and SECURITY control aspects
of IE to do with the issues on this page.From this
point it is possible to set levels of security.
OFFLINE SECURITY
Data on your computer system can be subject to virus attack even when your
computer is not connected to the internet. This can happen either by a virus
lying dormant on your system after being downloaded from the internet or
because it gained access to your system via a file added to your system from
a removable media,such as a floppy disk,CD or removable disk.
It is also good practice to make backups of any files that you have in case any files become corrupt.Copies of files that contain viruses would help spread the virus should those copies be used on another computer,it is therefore a good idea to make sure that an security backup copies have not got any viruses in them.
Points to remember about Security:
- Do not open Emails if you do not know who they are from -especially if they have attachments.
- Secure sites have a padlock in the corner of the webpage,but use common sense,don't give details away that can be used against you.
- Ciphering systems are in use on some webpages and email systems.
- Viruses need anti-virus software to keep your PC safe.
Child safety ad that led to porn site
BY MIKE TAIT |
| A HOME Office advert for a child protection website inadvertently directed people to porn, industry watchdogs revealed yesterday. The Government-sponsored radio commercial was publicising the thinkuknow.co.uk site, which advises children how to stay safe online. But a listener who wrongly typed the address as thinkyouknow.co.uk found links which led her to sites containing adult material and sexual services. The advert said: 'Giving out personal info could let a paedophile track you down. Be smart online, be safe online. visit thinkuknow.co.uk'. After investigating the complaint, the Advertising Standards Authority said the advert failed to make clear how the Web address was spelt. The ASA found the commercial in breach of its advertising code. It said the advert should not be broadcast again in that form and urged the Home Office to make the spelling of the Web address clear in future. 'This was particularly concerning as the ad was aimed at teenagers to help them stay safe online,' the ASA said. 'Although we recognised that there was no intention, we considered a significant effect of the ad was to indirectly publicise services unacceptable for broadcast.' The Child Exploitation and Online Protection Centre has since taken over the Home Office campaign. It defended the advert, saying inappropriate material was at least four clicks away from the misspelt website. However, it said it would comply with the ASA ruling. |
Beware of the screen grab |
|||
Internet theft is fast overtaking paper-based identity fraud as more information goes online.
By JAYNE ATHERTON
The Internet has become a potent weapon for identity thieves looking to get
their hands on thousands of pounds at a time. Few fraudsters bother to rifle
through bins for receipts, names and addresses any more. They can use a computer
to get the information they need in minutes.
Your ID is worth £85,0000
Phish and chips |

See also
The
Mathematical Tourist
Ciphering
Melissa
Hackers
Safe
Secret |